A group linked to Russian military intelligence, known as Fighting Ursa or APT28, has targeted at least 30 companies across 14 countries using a zero-day exploit in Microsoft Outlook (CVE-2023-23397). These organizations include vital infrastructure and sources of strategic intelligence, with a focus on military significance. The group has conducted multiple campaigns exploiting this vulnerability, emphasizing the need for enhanced security measures.
How to Tell If Your Computer Has a Virus and What to Do About It
Computer viruses, like real diseases, pose a threat by damaging programs, stealing data, and causing system crashes. To prevent infection, use trusted antivirus software, follow cybersecurity best practices, and be cautious with public Wi-Fi. If your computer is infected, run a full-system scan, restore to a backup, and consider reinstalling your operating system.
Cybercrime Group Exploiting Windows Driver Vulnerability to Bypass Security Products
Summary:
The cybercrime group Scattered Spider, also known as Roasted 0ktapus and UNC3944, has been targeting telecom and BPO firms by exploiting an old vulnerability in an Intel Ethernet diagnostics driver for Windows. They use phishing, social engineering, and BYOVD techniques to deploy malicious drivers and bypass security protections. Organizations should patch their systems and use endpoint security solutions.
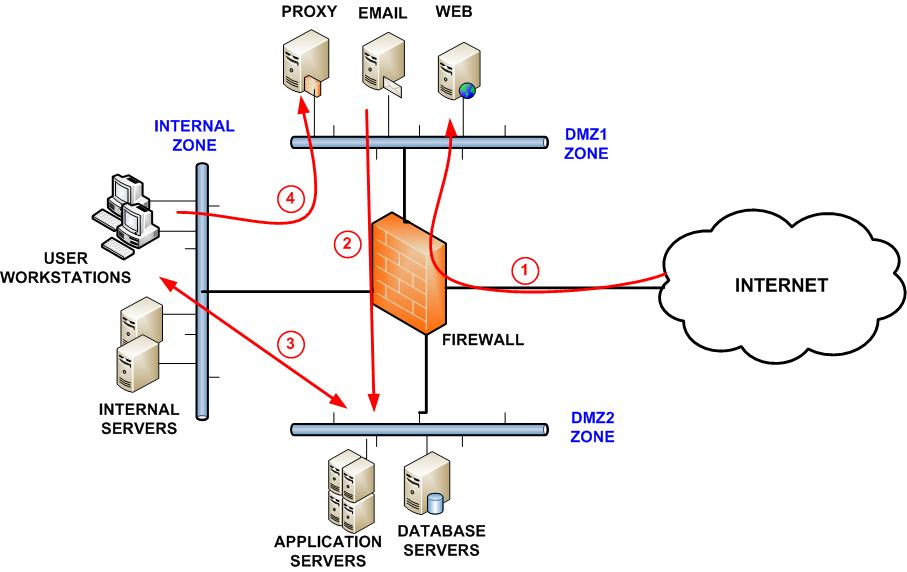
Network segmentation
Segmenting and securing your network is crucial for control and protection. Start by understanding your devices, users, data, and communication needs. Configure separate networks, gateways, DMZs, and access controls. Harden network devices, review regularly, and address remote, physical, and wireless access points. Don’t overlook configuring comprehensive logging for security events.
Microsoft Patch Tuesday: 97 Windows Vulns, 1 Exploited Zero-Day
Microsoft’s security patching machine hummed into overdrive Tuesday with the release of fixes for at least 97 documented software vulnerabilities, including a zero-day that’s already been exploited to escape the […]