Technology offers seniors solutions to aging challenges but also exposes them to cyber risks. Seniors’ internet usage is increasing, yet many miss out on its benefits due to safety concerns. Seniors should be cautious of scams, phishing, and data breaches.
ADRecon, a PowerShell tool to collect information about the Active Directory
I. Presentation In this article, we will discover the ADRecon tool for Active Directory Recon which will allow us to collect different information from an Active Directory directory. ADRecon will generate […]
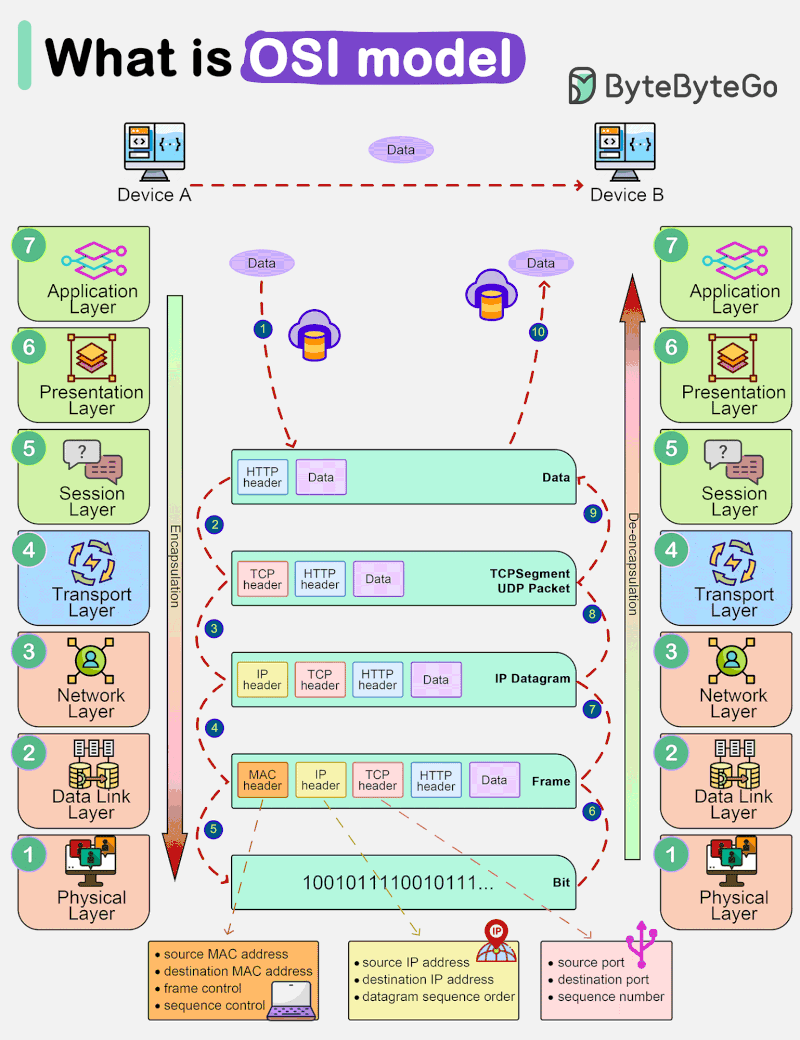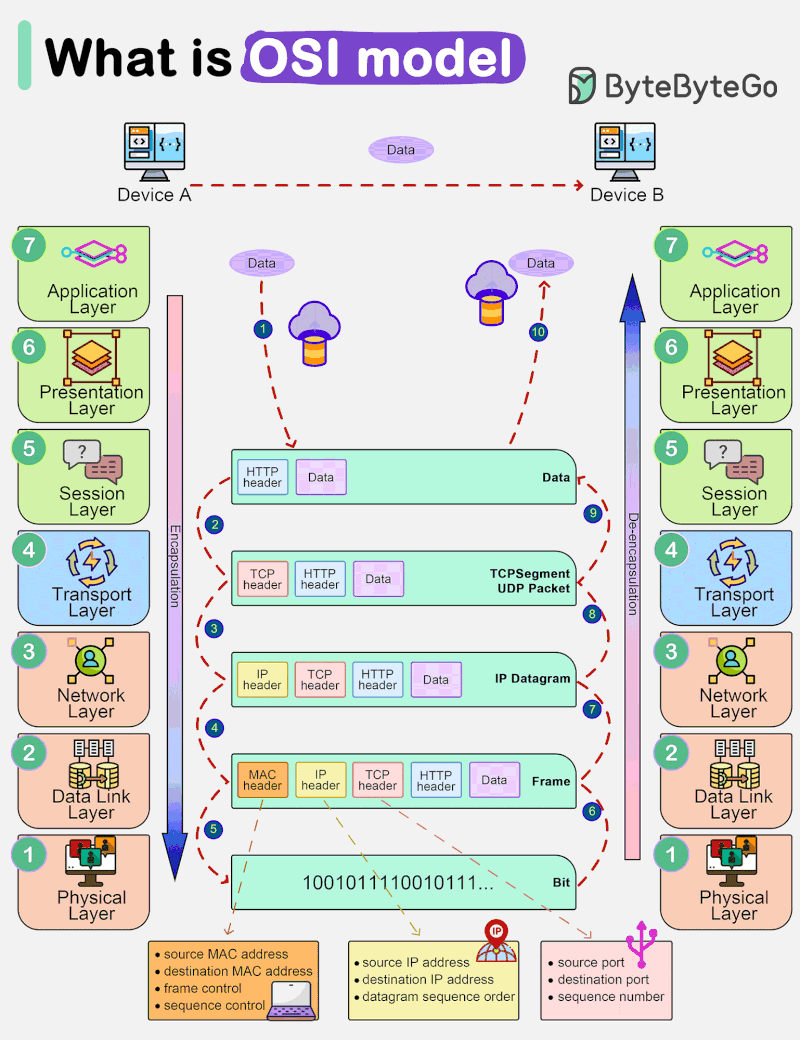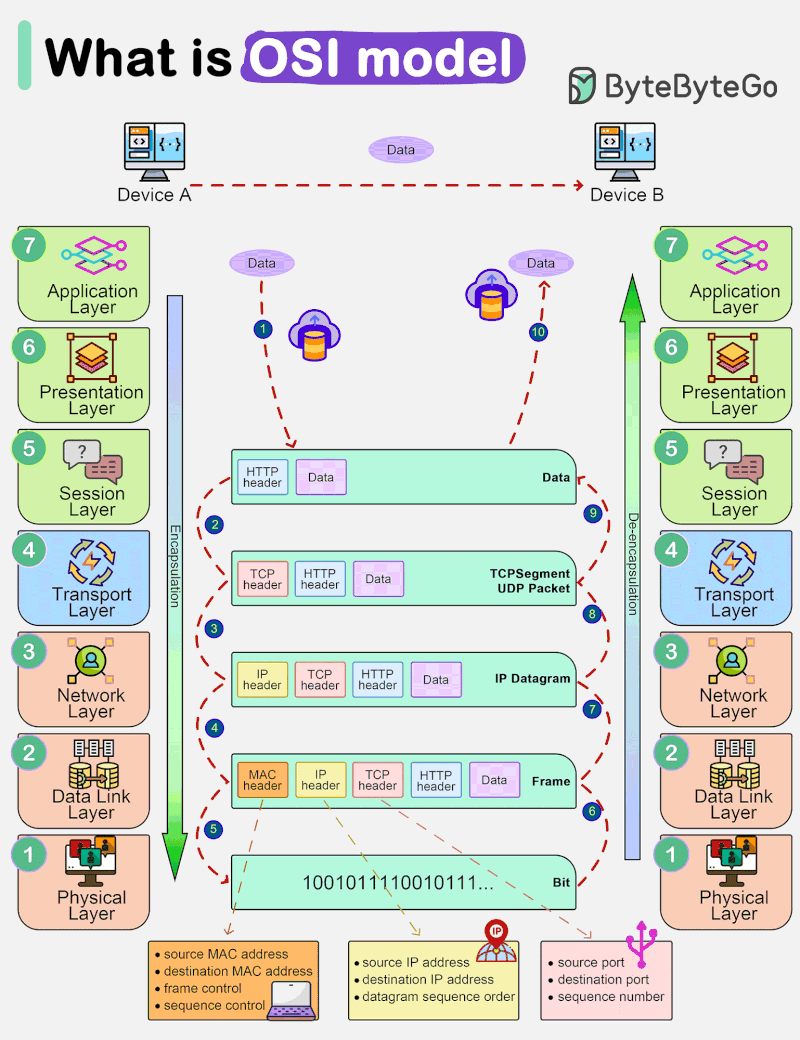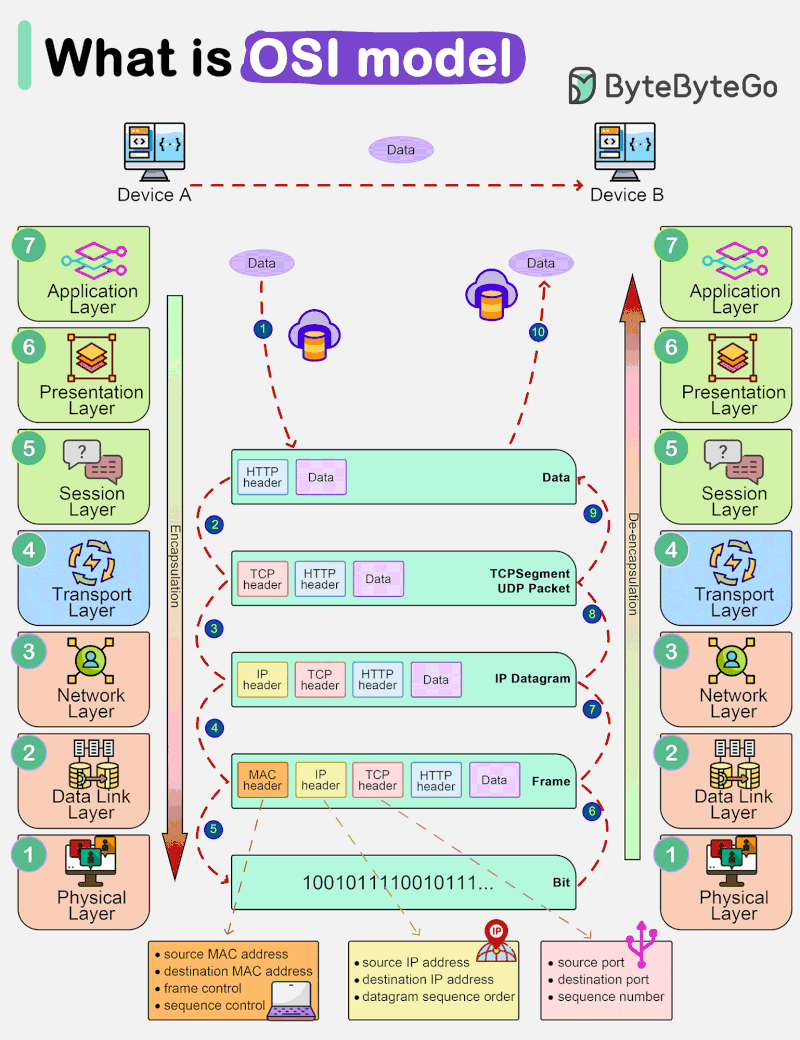
Networking and the OSI Model
Understanding the OSI model and TCP/IP is crucial for anyone interested in networking and the Internet’s inner workings. When you’re browsing the web or sending an email, remember that it’s […]
How To Automatically Set Up a Malware Analysis Lab using FLARE VM
Reverse engineering can be a challenging task, especially when it comes to creating a virtual machine (VM) and setting up the necessary tools. Fortunately, there are some great tools that […]
How to Build a Home IT Lab
A home lab is an invaluable resource for cybersecurity professionals to gain practical experience, develop and refine their skills, and stay current in a rapidly changing field.It is a playground […]
Top 10 Ransomware Gangs
Ransomware groups are rapidly evolving, using advanced tactics such as double extortion. They target high-profile victims with sophisticated malware, demand larger ransoms, and collaborate to hinder law enforcement. Notable ransomware gangs of 2023 include LockBit, Clop, and Royal, employing unique tactics like double extortion and extensive network access purchases.
Top 10 Cybersecurity Risks for 2024
Cybersecurity in 2024 presents complex challenges. Malware continues to evolve, AI-powered cyberattacks pose a threat, IoT vulnerabilities expand attack surfaces, and supply chain attacks target trusted relationships. Ransomware, zero-day exploits, biometric data breaches, and cloud security challenges also require proactive measures. Compliance demands, insider threats, and human error highlight the need for tailored defense strategies.
FREE Cybersecurity Certifications Trainings Online
The content includes free resources and courses related to cybersecurity, networking essentials, ethical hacking, digital forensics, and risk management. The list covers a range of topics including dark web, anonymity, and cryptocurrency, and also mentions certifications like CCNA Security. These resources can be valuable additions to a CV or resume.
Russian Hackers Exploiting Outlook Zero-day to Attack Critical Information Infrastructure
A group linked to Russian military intelligence, known as Fighting Ursa or APT28, has targeted at least 30 companies across 14 countries using a zero-day exploit in Microsoft Outlook (CVE-2023-23397). These organizations include vital infrastructure and sources of strategic intelligence, with a focus on military significance. The group has conducted multiple campaigns exploiting this vulnerability, emphasizing the need for enhanced security measures.
Cyber threats organizations need to watch out for, and some mitigation strategies.
Cybersecurity threats like phishing, ransomware, and supply chain attacks pose significant risks to organizations. Educating employees, implementing strong access controls, and regularly updating software are crucial preventive measures. In addition, encryption, incident response planning, and regular security assessments can enhance overall security. Staying informed and proactive is key in mitigating emerging threats.