The content includes free resources and courses related to cybersecurity, networking essentials, ethical hacking, digital forensics, and risk management. The list covers a range of topics including dark web, anonymity, and cryptocurrency, and also mentions certifications like CCNA Security. These resources can be valuable additions to a CV or resume.
Russian Hackers Exploiting Outlook Zero-day to Attack Critical Information Infrastructure
A group linked to Russian military intelligence, known as Fighting Ursa or APT28, has targeted at least 30 companies across 14 countries using a zero-day exploit in Microsoft Outlook (CVE-2023-23397). These organizations include vital infrastructure and sources of strategic intelligence, with a focus on military significance. The group has conducted multiple campaigns exploiting this vulnerability, emphasizing the need for enhanced security measures.
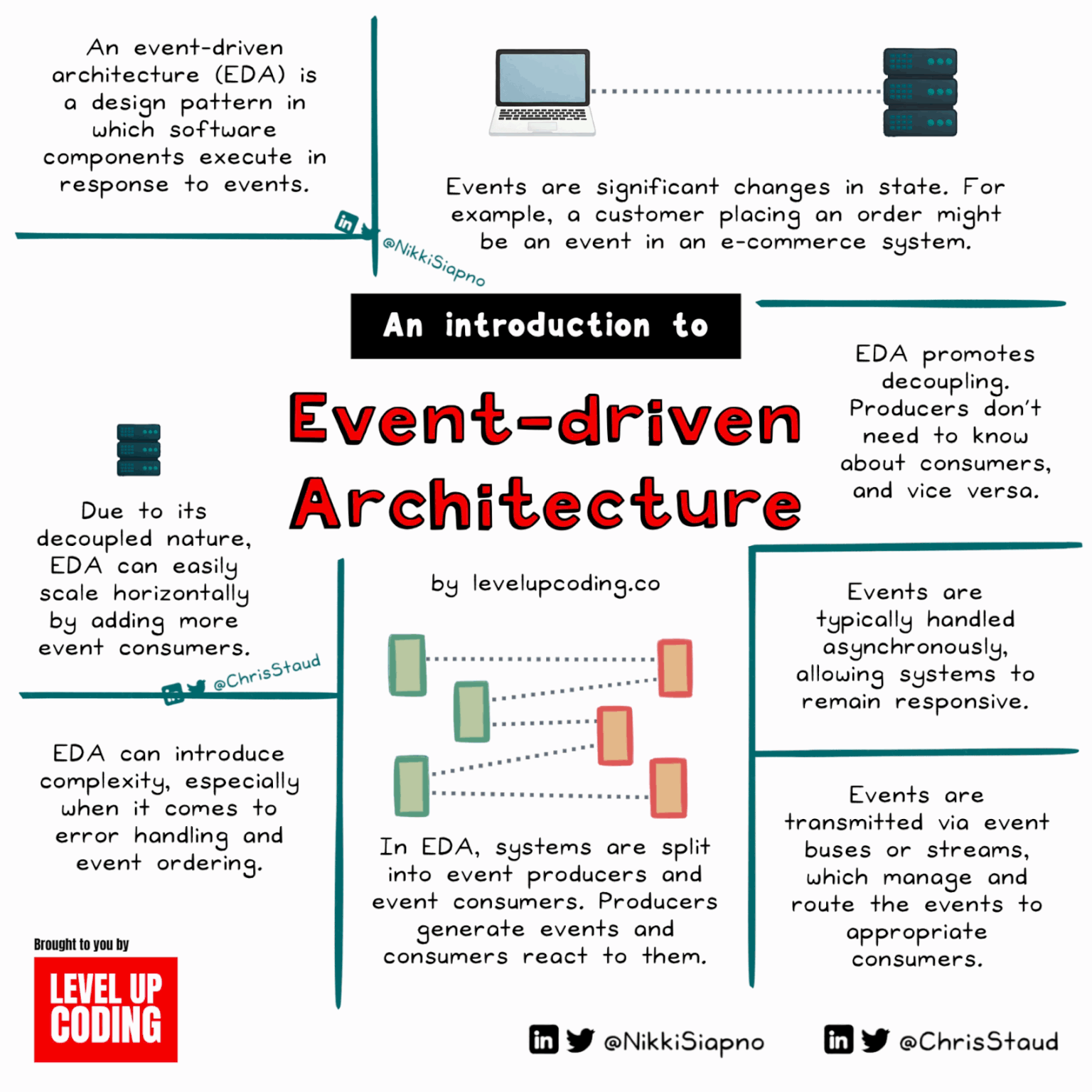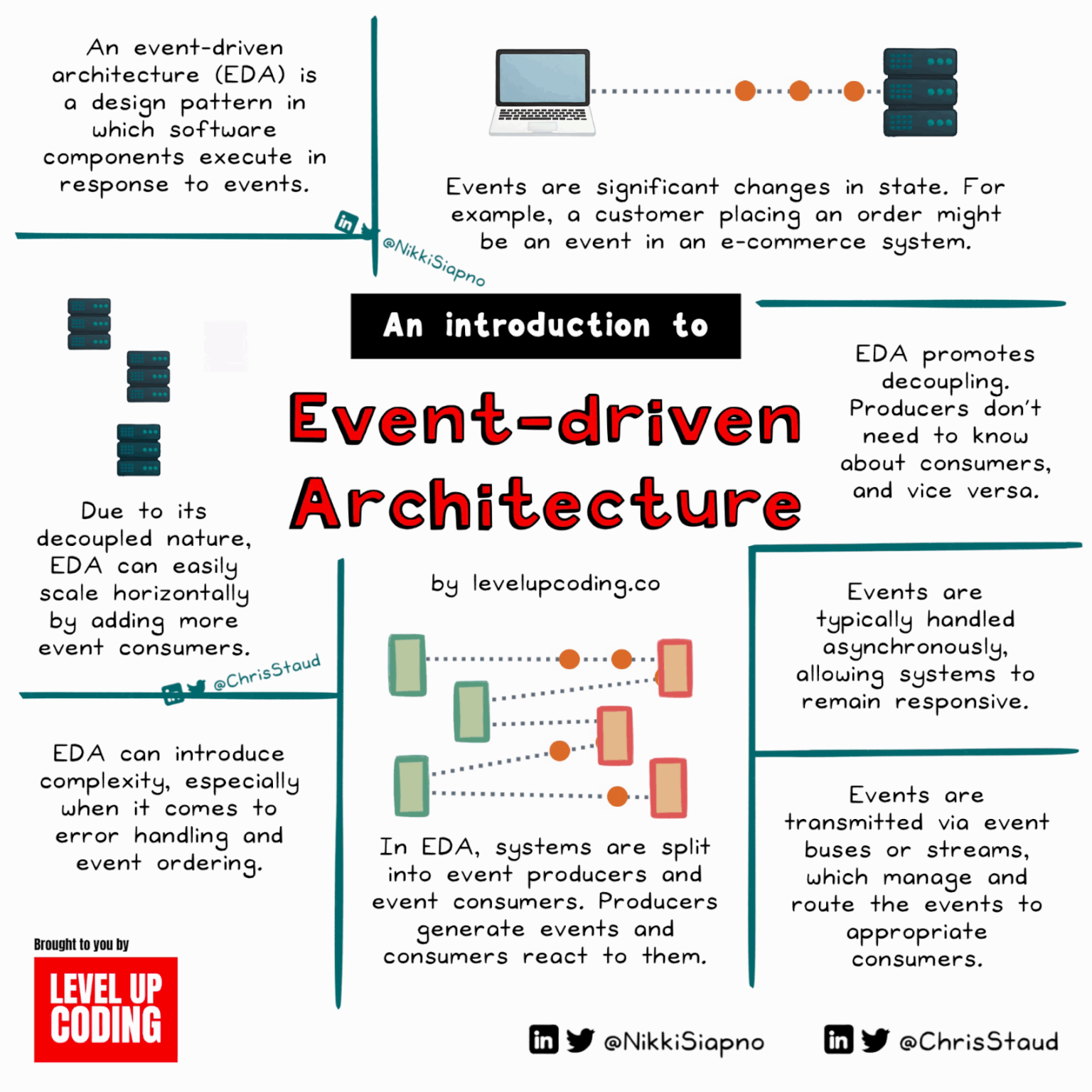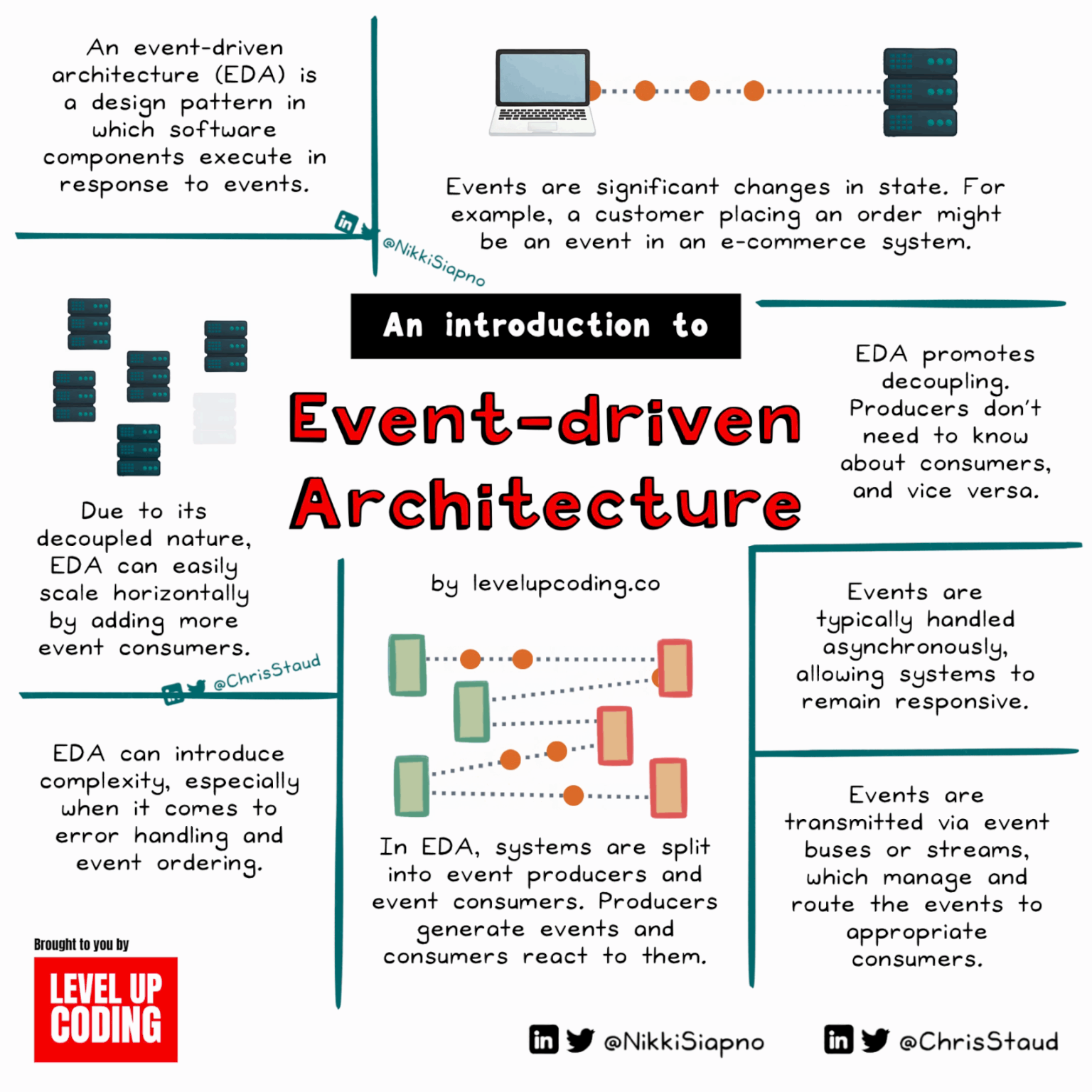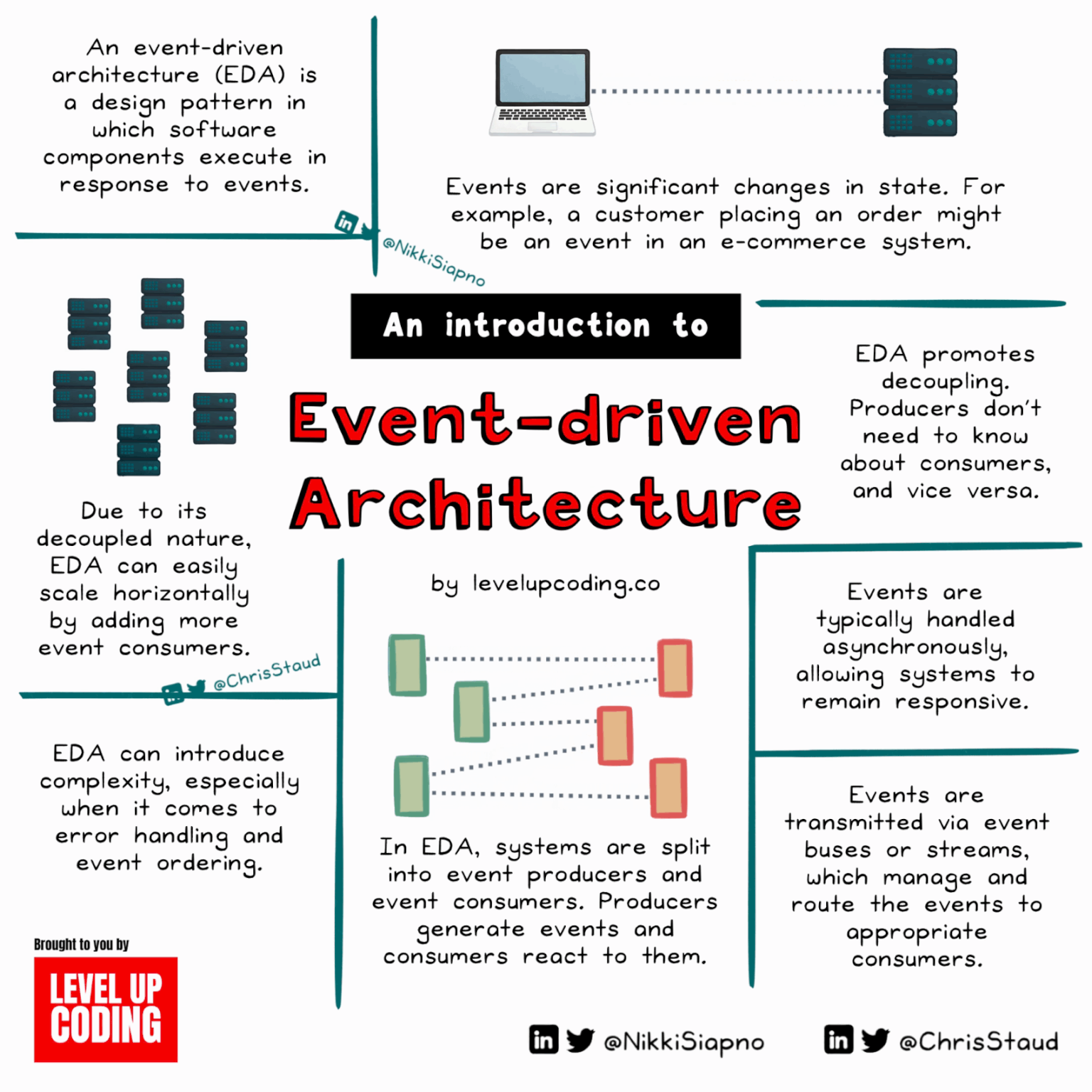
What Is Event-Driven Architecture, And How Does It Work?
Event-driven architecture (EDA) is driven by state changes, with events triggered by actions like adding items to a cart or liking a post. It comprises events, producers, consumers, and channels. EDA offers decoupling, scalability, real-time responsiveness, and resilience, beneficial for IoT systems, microservices, and real-time analytics. However, it brings complexity, event order challenges, and potential overhead.
Cyber threats organizations need to watch out for, and some mitigation strategies.
Cybersecurity threats like phishing, ransomware, and supply chain attacks pose significant risks to organizations. Educating employees, implementing strong access controls, and regularly updating software are crucial preventive measures. In addition, encryption, incident response planning, and regular security assessments can enhance overall security. Staying informed and proactive is key in mitigating emerging threats.
What to do when your Accounts have been Hacked!
If you suspect your digital account has been hacked, act quickly to regain control. Common ways accounts are compromised include phishing and data breaches. Signs of hacking include unauthorized posts or messages and notifications from companies. Take action by changing passwords, notifying contacts, updating security software, and seeking help from relevant authorities. Prevent future hacks by using strong, unique passwords, enabling multi-factor authentication, being cautious of phishing messages, and turning on automatic updates.
How to Tell If Your Computer Has a Virus and What to Do About It
Computer viruses, like real diseases, pose a threat by damaging programs, stealing data, and causing system crashes. To prevent infection, use trusted antivirus software, follow cybersecurity best practices, and be cautious with public Wi-Fi. If your computer is infected, run a full-system scan, restore to a backup, and consider reinstalling your operating system.
Cybercrime Group Exploiting Windows Driver Vulnerability to Bypass Security Products
Summary:
The cybercrime group Scattered Spider, also known as Roasted 0ktapus and UNC3944, has been targeting telecom and BPO firms by exploiting an old vulnerability in an Intel Ethernet diagnostics driver for Windows. They use phishing, social engineering, and BYOVD techniques to deploy malicious drivers and bypass security protections. Organizations should patch their systems and use endpoint security solutions.
How to take back control of a social media account
Social media has become essential for communication and business, but the risk of hacking is high. If you suspect an account breach, act quickly, change passwords, and report the incident to the platform. After recovery, review recent activity, inform followers, and fortify security measures. Use unique, strong passwords and enable multi-factor authentication to prevent future attacks.
Effective Online Safety for Everyone including Seniors
The Pew Research survey revealed that most seniors are active online and exposed to cyber threats. The Ultimate Online Safety Guide for Seniors offers advice on device protection, secure passwords, antivirus software, system updates, and privacy settings. It also provides tips to detect scams and stay safe on social media, online dating sites, and while shopping.
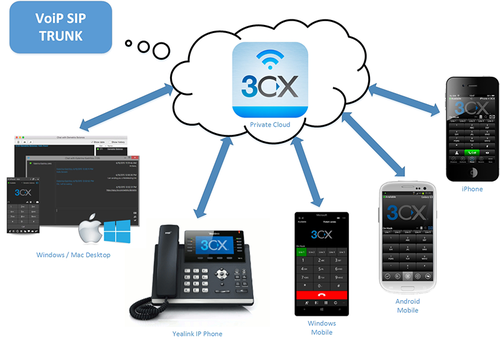
Elevate Your Business Communication with Farteck Solutions and 3CX!
Farteck Solutions offers 3CX for integrated communication, cost-efficiency, mobility, scalability, and advanced features like web conferencing, CRM integration, call recording, and analytics. The user-friendly interface and 24/7 support ensure a seamless experience.