Segmenting and separating devices on your network will allow your organization to have better control over access and security.
Your organization likely already has a network that has grown over time. This guide can help you set a design goal of what your network should look like, so you can break it down into smaller steps. You might want to start with segmenting part of the network that holds sensitive data as that will benefit the most. Your organization could also use this guide when building new networks, like cloud infrastructure networks.
Below are steps you can follow to design and build a segmented and secure network.
Understand the devices on your network
Before you can start breaking your network down into smaller networks, you need to understand what devices you currently have on it. This includes:
- Understanding what devices are connected. This could involve doing a network scan to identify everything that is currently plugged in and in-use. You can also cross-reference this list with an asset register if there are any devices that are currently disconnected.
- Understand who uses those devices. Knowing who uses those devices will be important when setting up your access controls. Be sure to differentiate who currently has access, and who needs access as part of their job. This could be a great opportunity to cut back access to follow the principle of least privilege.
- Understand what data they have. The sensitivity of the data these devices have access to will be a large driver in how you segment your network. For example, any credit card holder data must be separated from all other data because it carries a high security risk. You should separate any devices that have access to data you consider sensitive, such as personal, financial, classified, or intellectual property data.
- Understand what other devices they need to communicate with. These devices may need to send or receive data from other parts of the network. This is a great chance to understand which ports and protocols each device connects on as this will be a driver for the access control configurations. If you are unsure, perform a packet capture and analyze the network traffic using a tool like Wireshark.
Configure your networks
Once you understand what devices are used, who uses them, and what data they have, you can start configuring your segmented networks. Your organization’s network design will be unique. Here are a few things to keep in mind when configuring yours:
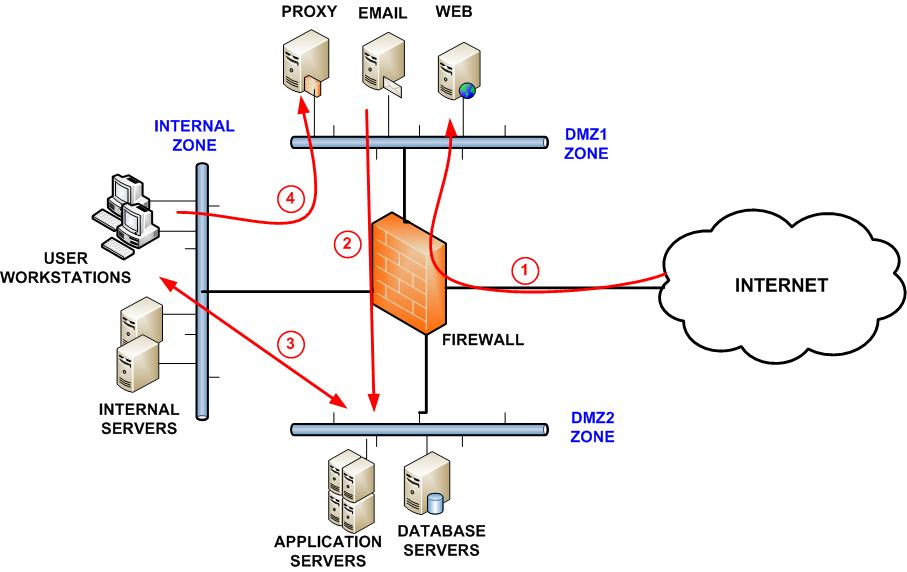
- Create separate networks for each group of devices that hold sensitive data. For example, you will have a separate network that contains credit card holder data, a separate network for your finance team, and a separate network for all other business functions.
- Use gateways in-between your networks. Control access in-between your segmented networks using gateways. These gateways may have different features that allow you to inspect and filter the traffic. You could use a gateway, such as a web application firewall, in front of the network with your web servers in order to filter out malicious traffic. A gateway with access control capabilities is important for controlling access into your sensitive networks so you can enforce things like multi-factor authentication.
- Use a demilitarized zone (DMZ) in between the internet and your networks. Some services – such as web or mail servers – will need to allow inbound connections from untrusted networks like the internet. These services can be kept in a DMZ, a semi-trusted network that your organization controls. You can then use gateways to control and filter the traffic as it passes between your sensitive networks, the DMZ, and the internet.
- Separate your management and data interfaces. Management and data interfaces should be separated either virtually or physically. Management interfaces are often used for carrying out privileged and administrative functions. You might consider having them only accessible from a separated, sensitive network that can only be accessed by the appropriate administrators.
- Use security features that can’t be spoofed or bypassed. If you are depending on security features to limit authorized access to sensitive networks, make sure the features are configured so they can’t be spoofed or bypassed. For example, VLAN hopping is a common attack where an attacker can move from one VLAN to another by attacking a misconfigured switch directly. If there are inherent weaknesses in the network devices you are using, make sure there are other security controls you can put in place to limit the risk of unauthorized access.
- Create a network for any legacy systems. Network segregation can be a great way to control and lock-down access to any legacy systems you might be running. A gateway could be used that scans for specific vulnerabilities that the legacy system may be exposed to and prevent that system from being compromised.
- Configure access controls to separate your networks. Each gateway should only allow the ports and protocols that are required by the devices in the networks they connect to. All other ports and protocols should be closed and denied. This means operating based on an allowed list instead of a block list. Access controls to sensitive networks should take it a step further and use user-based access policies and multi-factor authentication.
Harden all network devices
Regardless of how your network is designed, all of its network devices need to be hardened and maintained. These network devices have a big role to play in keeping your network secure so they need to be protected. They should be secured and maintained the same way you would maintain other assets and systems in your network.
A lot of the other critical controls apply to hardening these devices:
- Before a device is installed onto the network, it should be patched and have any default or generic accounts disabled.
- All devices on the network should be patched regularly, and replaced when it is no longer supported by the vendor.
- Access to these devices should be restricted to only the people who need to maintain the device and it should be physically protected.
- All device ports and services that are not going to be used should be disabled.
As well as applying controls between networks, each device should run a local host-based firewall, to ensure that attackers are limited within the network segment as well. The default rule for a network device should be to deny traffic so that a connection is only permitted if there is a specific allow rule set for it.
A regular review of these network devices will allow you to catch issues like misconfigurations. Network devices should be reviewed at least once a year to make sure they are still hardened, and that all their configured network rules are still necessary.
Consider remote, physical, and wireless access points
Your organization likely has a wireless network in the office that you use for staff and guests. If they don’t use wireless, they will need to have a physical port to connect to via ethernet. You will need to understand what each user’s requirements are and determine which networks these connect to.
Guests likely just need access to the internet, so they could be on a small network by themselves that is separated from all your other devices. This small network likely just needs an outbound connection to the internet. Staff access can be a bit more complex as they might need the same access to various devices and networks in the same way their ethernet-connected docking station or desktop is setup. Wireless access points shouldn’t be setup directly on networks that hold sensitive data. Instead, the user should be placed in a network that has access to basic devices (such as the intranet) and have to go through different access controls in order to get to that network.
If physical ports are used, make sure they are not in open, public places. Port-based authentication can help prevent unauthorized people from just plugging in and gaining access, and physical security adds an additional layer of protection. This also helps manage the risk in case the port-based authentication settings are misconfigured or the protocol becomes vulnerable.
Regardless of the type of network connection used, a user should be required to authenticate before gaining access to the organization’s network. For authenticating to the segmented guest wireless network, you could use Wi-Fi Protected Access 2 (WPA2) Personal and a strong passphrase. For physical port-based authentication or the staff wireless network, you should use something that can’t be shared like WPA2 Enterprise with 802.1x authentication.
If you provide a remote access tool, like a virtual private network (VPN) server to your staff, you will need to consider which network it drops the user into. You will want to add additional layers of security, like multi-factor authentication, since the user will be coming from the internet. With physical or wireless access, an attacker would need to be physically close to your organization’s network. With remote access, anyone can try knocking on the door to your network and try to get in.
Configure logging
Logs from the network devices should be configured and sent to a central place for analysis. The type of events that are captured will depend on the network devices used. Some devices are able to analyze traffic and produce more detailed security events (like vulnerability exploit attempts). Most devices should be able to provide basic security events (like failed logins).
If possible, the following security events should be captured:
- changes to network device configurations, policies, or rules
- changes to users who have access to the network devices
- failed multi-factor authentication attempts
- suspicious or multiple failed logins to the network devices or to segmented networks
- suspicious traffic, either blocked or allowed.
source: CertNZ