Using a zero-day exploit in Microsoft Outlook (tracked as CVE-2023-23397), Fighting Ursa Aka APT28 targets at least 30 companies across 14 countries that are probably significant sources of strategic intelligence for the Russian government and military.
All 14 countries targeted in a total of three campaigns are institutions within NATO member countries, except those in Ukraine, Jordan, and the United Arab Emirates.
These organizations included vital infrastructure and sources of information advantage in the domains of diplomacy, commerce, and military affairs.
The following target organizations were among them:
- Energy production and distribution
- Pipeline operations
- Material, personnel, and air transportation
- Ministries of Defense
- Ministries of Foreign Affairs
- Ministries of Internal Affairs
- Ministries of the Economy
Zero-Day Exploit in Microsoft Outlook
With this vulnerability, Fighting Ursa conducted at least two campaigns that were made public. The first took place in March 2022, and the second took place in March 2023, between March and December 2022.
Researchers from Unit 42 have uncovered a third, current campaign in which Fighting Ursa exploited this vulnerability as well. The group’s most current effort, which targeted at least nine organizations across seven countries, was executed between September and October of 2023.
APT28, Fancy Bear, Strontium/Forest Blizzard, Pawn Storm, Sofacy, or Sednit are other names for Fighting Ursa, a group connected to Russian military intelligence that is well-known for focussing on targets of Russian interest, particularly those with military significance.
Russia’s military intelligence unit 26165, the 85th Special Service Centre (GTsSS) of the General Staff Main Intelligence Directorate (GRU), has been credited with fighting Ursa.
Fighting Ursa sent an email with the first known example of an exploit targeting the State Migration Service of Ukraine by leveraging the CVE-2023-23397 vulnerability, which at the time was a publicly unknown zero-day exploit.
CVE-2023-23397 is a vulnerability in the Windows Microsoft Outlook client that can be exploited by sending a specially crafted email that triggers when the Outlook client processes it. The exploit requires no user activity to be activated.
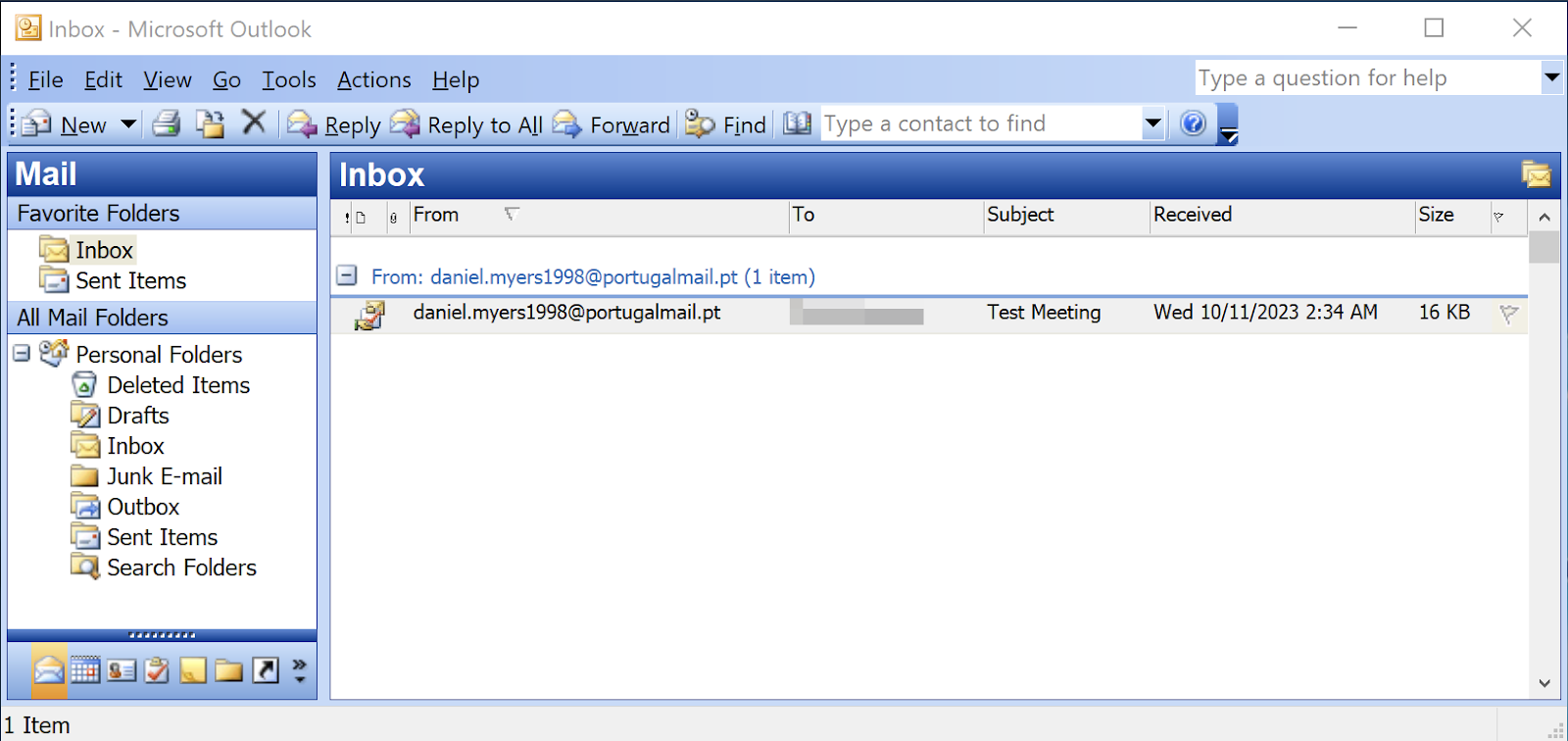
“Successful exploitation of Microsoft Outlook using this vulnerability results in a relay attack using Windows (New Technology) NT LAN Manager (NTLM) as described in our threat brief for CVE-2023-23397”, researchers said.
For two main reasons, researchers link Fighting Ursa to the actions within these campaigns:
- The Russian military appears to value the intelligence gathered from the targeted victims of these activities.
- Similar to earlier Fighting Ursa efforts, all of the campaigns harvested NTLM authentication messages from victim networks by using co-opted Ubiquiti networking devices.
Recommendation
- Pay attention to these attack strategies
- Address this vulnerability
- Set up endpoint security to prevent these kinds of malicious campaigns.
Source: cybersecuritynews.com