The internet can be a scary place, especially if you’re old enough to be able to remember dialing a rotary telephone! In 2020, in the US alone, cyber crimes against adults aged 60 and over resulted in approximately $1 billion in losses — a 30% increase over the losses reported in the previous year. Of the almost 800,000 complaints of cyber crime reported to the FBI’s Internet Crime Complaint Center (IC3) in 2020, over 200,000 victims were over the age of 60.
Staying safe online can be really overwhelming — most users have their photos, credit cards, personal communications, financial information, and devices exposed to hackers every single day without even knowing that they’re in danger.
In this article, I’m going to explain the most common online threats facing seniors today, such as:
- Viruses and malware.
- Phishing.
- Data breaches/password theft.
- Social media scams.
- Banking fraud.
- Privacy violations.
- And more…
If this list has made you feel nervous (and you’re getting ready to unplug all of your devices and go back to your rotary phone), don’t worry! The vast majority of cyber attacks can be easily prevented with the proper tools, some basic education, and plain old common sense.
Most seniors don’t know the difference between ransomware and a random number generator — which is why the best security software has been designed for even non-tech savvy users. In addition to defining the most dangerous cyber threats (and giving you practical tips to avoid them), I’ve personally selected highly secure antivirus programs, password managers, and even virtual private networks (VPNs) that can keep you safe with a minimal amount of setup and that are very easy to use.
So whether you’re looking for the best deals for rotary phones on eBay, trying to figure out why strange Russian girls are trying to sell you Ray-Bans through Facebook Messenger, or you just want to safely keep up with family, friends, and finances online, look no further — my ultimate internet safety guide for seniors is your one-stop shop for internet security assistance in 2023.
What Are the Most Common Online Threats Affecting Seniors?

Seniors face pretty much the same risks online as everybody else — hackers have an ever-expanding array of tools to fleece users out of their money, steal user data, destroy devices, and spread dangerous files and scams across the web.
Some common online threats affecting seniors are:
- Malware. Software designed to damage a computer, steal data, or financially exploit unsuspecting users. Common malware types include ransomware, trojans, and spyware (we will discuss these more later in the article).
- Data breaches. The release of personal information (such as email addresses, usernames, passwords, and even credit card numbers and social security numbers) to the general public and dark web servers. Recent high-profile data breaches have affected millions of Facebook and LinkedIn users.
- Scams. Hackers are constantly coming up with new ways to deceive users into giving away their personal information and money, including scam emails, text messages, websites, social media accounts, and online dating profiles.
- Identity theft. Using another person’s personal information (e.g. name, social security number, credit card, etc.) without permission.
Fortunately, a lot of these attacks can be prevented with a few simple tips and by following a few simple steps, and I will also show you what to do if you unfortunately fall victim to cybercrime.
How to Best Protect Yourself (& Your Personal Info) Online
Download a good antivirus program. Using good antivirus software is the easiest way to stay safe online. The top antiviruses on the market include real-time malware protection to block viruses before they can run, anti-phishing tools to block scam websites, and additional extra features like firewalls, Wi-Fi scanners, VPNs, password managers, software updaters, data breach monitors, and more. Norton is my #1 antivirus choice — it’s really easy to use and provides a ton of automatic security tools to keep all of your devices safe.
Always go to the source. Hackers use deceptive pop-up windows, email links, text messages, websites, phone calls, and more to try and rush and pressure users into bad decisions. Maybe a legitimate government agency really is texting you, or your utility company sent you an email, or your old friend wants you to download an email attachment. But you should always try to confirm that the information you’re getting is authentic by using a trusted contact method like giving that agency, company, and friend a call. Always be skeptical — if it sounds too good to be true, it probably is!
Only go on secure websites. A website is considered secure if the address starts with “https://” (instead of “https://”). A quick way to check if the website is secure is to look for the padlock icon next to the address bar, which indicates the website you’re using has a secure encrypted TLS connection (you can learn more about web encryption and security in our blog post about man-in-the-middle attacks). The HTTPS Everywhere browser extension is a great free tool to help ensure you’re using encrypted web connections whenever possible.
Avoid pirate sites. Downloading (or torrenting) music, movies, and TV shows for free is tempting, but it’s best not to use torrenting websites. These websites are generally unsafe and they’re always full of malicious links and malware downloads. If you do download pirated content, make sure you’re running a powerful antivirus program with effective real-time malware detection. It’s also good to use a VPN when downloading files — a VPN hides your actual IP and prevents your internet service provider from monitoring your online activity (ExpressVPN is my favorite VPN for torrenting).
Use a variety of passwords. The best way to keep online accounts safe is to use different and complex passwords for each account. Remembering so many different passwords is difficult, so it’s advisable to use a password manager. Read about our favorite password managers here — my personal favorites are 1Password and RoboForm.
Keep your system updated. It’s important to keep your operating system and programs updated as software developers are constantly patching security vulnerabilities. I recommend you set your computer to automatically install updates when they become available. If you don’t keep your device updated, you’re at risk of exploit attacks, which is when hackers can take advantage of a known security weakness. You can learn more about exploit attacks here.

Don’t be afraid to ask for help! Computer running slowly? Weird email? Incredibly cheap products? Strange notifications? Make sure you have a trusted family member or human to speak with. And some antiviruses like Norton have a remote access tool, which allows tech support operators to get into your computer and solve problems 24/7.
How to Spot Online Scams

According to the FBI and the National Council on Aging (NCOA), some of the most common online elder fraud scams are:
- Romance scams. Criminals pose as interested romantic partners on dating websites or social media, and exploit seniors for money. IC3 reported that seniors lost over $280 million to romance scams alone in 2020.
- Lottery and charity scams. Hackers appear to represent legitimate charities, lotteries, or sweepstakes and then convince seniors that they have won a contest or persuade them to make a donation.
- Tech support scams. Criminals claim to be tech support and flag a fake computer or mobile device issue. They offer to solve the problem by using a program to take over a device to gain personal information.
- Grandchild scam. Criminals pose as grandchildren who ask for financial assistance.
- Government impersonation scam. Criminals claim to be government employees and demand payment or personal information regarding taxes, social security, pensions, etc.

Most of the time, online scammers will be very insistent and demand that you act quickly, whether it’s giving them access to your device, giving them personal information, or sending them money. It’s important that you resist the pressure to act out of urgency and take the time to assess the situation properly. Here’s a few techniques you can use to determine if you’re communicating with a legitimate person or a scammer:
- Don’t click on links and don’t download anything. If you’re even slightly suspicious about the communications you’re receiving, don’t follow any links or download any files. Unsafe links and files can steal your data, damage your devices, and much more. Good internet security software like Norton can block unsafe links and suspicious downloads in real time.
- Go to the source. Google the charity, lottery, tech department, or even government office potentially being impersonated. You can usually contact these organizations via phone or email and verify if you’re being contacted by a scammer or an honest person.
- Ask yourself clarifying questions. Ask yourself, “Why would a tech support person need you to download a file? Or, “How did you win a sweepstake that you never entered in the first place?” By asking yourself these types of questions, it will likely expose whether the message is from a legitimate source or not.
- Use Google. Most scammers aren’t very creative. There’s a good chance the scam being run on you has been used before — copy-paste text from an email, or just type in a few words describing your situation, followed by the word “scam”, and see if the same scam has been attempted on other people.
Scammers reach out to users via phone call, text message, email, and even plain-old snail mail. But one of the most common and dangerous techniques is called phishing.
Phishing
Phishing is the act of creating fake websites, phone numbers, or email addresses that mimic legitimate sources for the purpose of getting information, stealing money, or deploying malicious programs on user devices.
The first major phishing attacks occurred in 1996, when a hacker program called AOHell was released. AOHell had the ability to send out fake mass emails to America Online users, which essentially said, “this is AOL customer support, please reply to this email with your username and password to verify your account”. Similar to a weekend fishing trip, these attacks sent out thousands of lines, but only succeeded in catching a few victims willing to provide their account information. Thus, phishing was born.
Nowadays, millions of phishing messages are sent every day via email, social media, or text message (known as ‘smishing’). These messages may inform you that you have money waiting for you, ask you to fill out a survey, or may even trick you into reimbursing a government or financial institution.
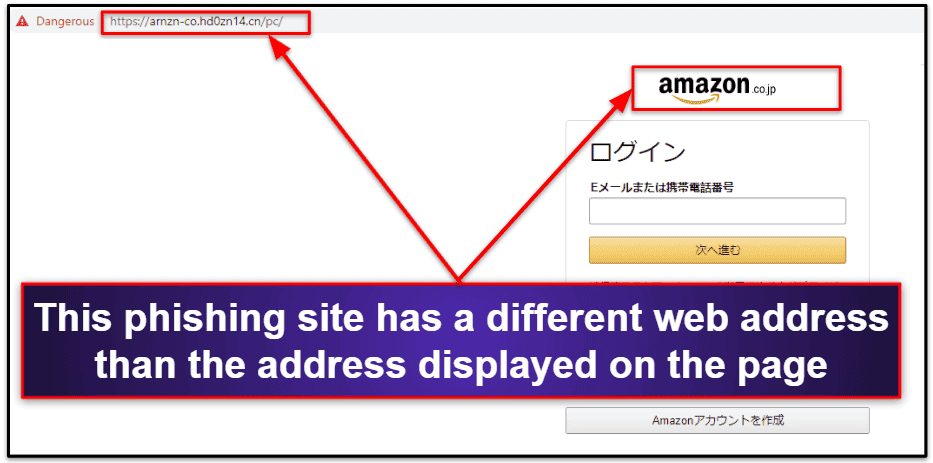
The Anti-Phishing Working Group reported over 600,000 phishing attacks in the first quarter of 2021 alone. And according to IC3, in 2020, seniors lost over $18 million from phishing and smishing-related scams.
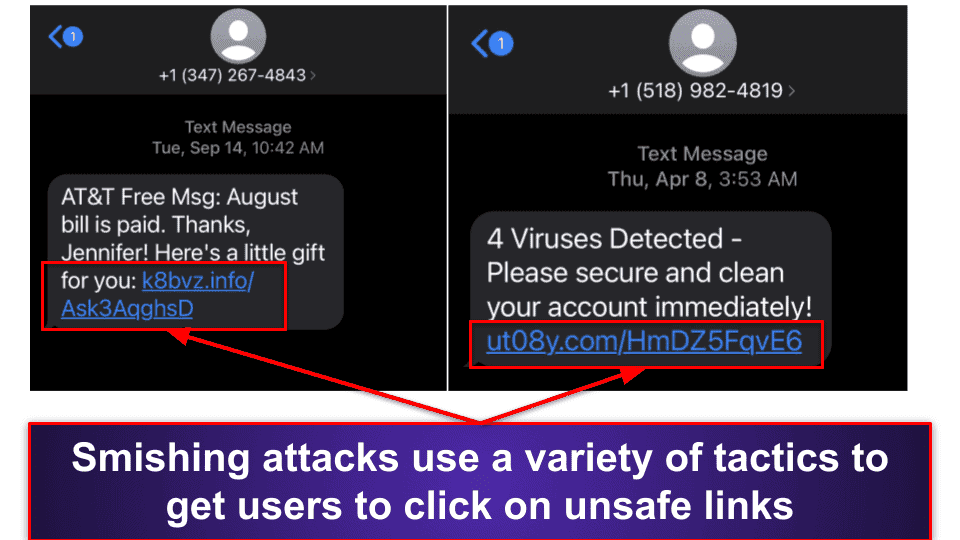
Identifying phishing attacks can be tricky, as phishing messages can look very official and will often link to websites that are pretty convincing copies of legitimate sites. Banking websites and online retailers are very commonly imitated for phishing attacks.
Most of my tips for spotting the online scams above will work to help you identify phishing sites, but here are some specific tips to help you if you feel like you may be the target of a phishing attack:
- Don’t click on links. Phishing messages and smishing messages frequently contain links that can lead you to unsafe sites.
- Check the email address and not just the sender name. It’s really easy to deceive someone with a fake sender name when sending emails. When this happens, the sender name may be familiar, but the email address doesn’t match the sender name. For example, in my spam folder I have many emails from “Walmart.com” but the email address is “njqksp93tgq9.22y3kr01zrrkif8jahx8@2djfji.6az9yc29rg.us”. If the email was actually from Walmart, the email address would be from “@walmart.com”.
- Look for typos. Phishing attacks frequently use similar spellings as the brands they are trying to spoof, for example “amazn.com”, or “support@micr0soft.com” to fool users.
- Use Google. Look up the organization being imitated on Google, and compare the legitimate website to the potential phishing site.
Phishing pop-up ads that appear while you’re browsing the internet are also very common. Some ads will ask you to claim a prize, or you may even receive a fake notification from Microsoft or Apple claiming something is wrong with your device. It’s best to not click on any pop-up ads that appear on your screen and simply click on the X in the corner to close the window — legitimate Windows notifications don’t pop up in the middle of your browser screen.
Don’t assume that only strangers can send you phishing messages. Real accounts can be hacked and it’s possible to receive phishing messages from your friends. Look out for impersonal, vague, or out of character language in the message. And if you do receive a message or email from a friend asking you to click on a link, follow the steps above to try and determine if you’re being phished. Also, if possible, simply reach out to your friend with a phone call or text to determine if they sent you the message.
How to Respond to Identity Theft
Identity theft can be glaringly obvious — for example, if somebody starts spending all of your money or maxing out your credit cards. But some identity theft is a lot more subtle, with small purchases or loans being taken out without victims ever noticing.
So, what should you do if you’ve already been attacked, and cyber criminals have gained access to your accounts?
Of course, the first step is to notify all of the relevant financial institutions and cancel your credit cards so that criminals can’t continue spending your money! However, if you’ve been extensively hacked, scammers will still be able to access your accounts and steal any new card numbers or account information as long as your device is compromised.
The good news is you don’t need to throw your computer out the window! You need to close up all of the backdoors in your system, but this could be challenging for advanced and inexperienced users. So, I highly recommend you use a professional identity theft protection service to assist you with this process.
Norton LifeLock’s identity theft protection is the safest choice for anyone in the US. It includes insurance against identity theft losses and live phone assistance with making the necessary changes to compromised accounts. LifeLock tech support staff can even use remote access tools to log into your computer and remove any malware that hackers may have installed on your device.
Users in Canada and the EU can use McAfee’s identity theft protections, which use international credit bureaus to monitor and detect fraudulent use of your accounts.
If you’re outside of these nations, I suggest that you quickly follow the steps below, and also seek help from your bank or financial institution.
- Notify your bank. Your bank will immediately freeze your accounts, preventing any further losses, and it will also begin the process of reimbursement for the funds stolen from your account.
- Run an antivirus scan. It will detect and remove any surveillance malware from your device that could be used to steal future financial information and prolong the identity theft attack. Make sure you’re using a reputable antivirus program like Norton or Bitdefender.
- Change your passwords. Once your system is free of malware, change your passwords. I recommend using a high-quality password manager for this process, like 1Password.
- Bookmark this article. Make sure you refer to this article to prevent falling victim to future attacks, and for knowing what steps to take in the event you become a victim to cybercrime.
Identity theft attacks can occur when users fall victim to a scam, but they can also happen without any user error — like when a user’s information is leaked in a data breach.
Data Breaches
Data breaches occur when a hacker breaks into a company’s servers, steals the company’s data, and publishes the private data stored by that company — this information can include millions of usernames, passwords, personal information, and even financial information. Sometimes, the data from these breaches is exposed publicly, with everyone on the internet simultaneously gaining access to this information, while others breaches are secretive, with the information being shared among hackers in the dark web for weeks or months until the breach is discovered.
Breaching major corporations is seen as an accomplishment for hackers, almost like big-game hunting. There’s constant competition among hackers to take down the biggest targets, with little regard for the real-world consequences experienced by everyday people whose information will wind up all over the web.
Data breaches are becoming increasingly common: in 2013, Yahoo was hacked and 3 billion records were exposed. In 2021, information from 530 million Facebook users got publicly leaked. Financial institutions aren’t immune either — in 2019, 885 million First American records were breached, exposing bank transactions, social security numbers, and more.
So, data breaches are scary, but what can you do about them?
There’s nothing an average user can do to prevent Facebook from getting hacked, but there’s a lot you can do to keep yourself safe in the event that your information has been breached:
- Use unique passwords. If you have a different password for each of your online accounts, then a data breach won’t result in a devastating privacy violation when hackers get their hands on one of your account passwords. If you have the same password for most of your accounts, hackers can use that password for multiple sites to gain access to your accounts.
- Change your passwords regularly. Many breaches go unreported for months before being found, so it’s smart to be proactive and constantly change your passwords. It’s quick and easy to update your passwords with a password generator — most password managers like 1Password have excellent password generators.
- Use a breach monitoring tool. You can manually enter your emails and usernames into haveibeenpwned.com, which is a massive public registry of all of the publicly available breached account information. Norton also includes a built-in data breach monitoring tool with its 360 package. Many password managers like Dashlane and Keeper also have data breach monitoring and alert you if your email was involved in a breach.
If the idea of memorizing unique passwords for dozens of websites, constantly checking for data breaches, and regularly coming up with new passwords seems daunting, you’re not wrong! That’s why the vast majority of privacy experts online, including Edward Snowden, recommend using a password manager to create, store, and automatically fill complex and randomly generated passwords. I’ll tell you all about password managers in the next section, but I’ll tell you now that 1Password is my favorite password manager for security, price, and ease of use.
How to Keep Your Passwords & Online Accounts Secure

Password security is incredibly important, and it can actually be pretty easy to maintain good password hygiene with the right tools. Simple passwords like birthdays or your pet’s name and a zip code can be cracked by hackers in under a minute. And if you use the same password for every account, once that password is found, all of your accounts are compromised.
Having a password manager is a great tool to keep you safe online.
Password managers work for Windows, macOS, iOS, and Android devices — they generate unique passwords, they store all of your passwords in one securely encrypted vault, and they can automatically fill passwords, addresses, financial information, and more with a single click.
For example, I use 1Password on my PC, iPhone, Chromebook, and Samsung Galaxy tablet. Whenever I open my browser on my PC, I log into 1Password using my master password, which is a secure password that only I know (it’s not stored on 1Password’s servers anywhere). Once I’m logged into my password vault, 1Password’s logo pops up in any login field whenever it sees a website it recognizes — I simply tap the logo and watch my username and password fill in automatically. When I’m creating a new account, the same thing happens except that when I tap the 1Password logo, it brings up a secure password generator, which automatically creates a unique password and saves that password in my vault.
All of these passwords are synced in real-time across all of my devices, and I can even log into 1Password on most of my devices with a quick fingerprint scan. I don’t have to worry about memorizing passwords, losing passwords, or having my passwords cracked by hackers — 1Password does all the work for me and uses advanced technology to prevent criminals from accessing my account.
Here are the most important features to consider when looking for a password manager:
- Secure encryption. By encrypting your data, password managers ensure that there is no way for your information to be stolen in a data breach. 256-bit AES encryption is the industry standard, but some apps use 128-bit AES or XChaCha20, which are also good.
- Two-factor authentication (2FA). A required second step to log into an account after entering your password. This could be a temporary one-time password, a USB token, or a notification sent to your phone.
- Password auditing. Flags weak and repeated passwords in your vault so you know exactly which passwords you need to change in order to stay safe online.
- Data breach monitoring. Automatically notifies you if any of your saved logins have been breached.
- Biometric login. Log into your password manager using a fingerprint or face scan.
- Secure password sharing. If you’d like to share your password with your partner/spouse or trusted caregiver/family member, a good password manager can help you share logins securely rather than sending your password through a text message or email.
You can learn more about password managers by checking out our list of the best password managers in 2023.
How to Use Emails Safely

Over the last 3 years, victims over 60 have lost more than $500 million due to reported email-related scams. Here are some tips to keep you safe while using your email.
Always check the sender’s email address to make sure it’s coming from a legitimate source. Look out for addresses that look similar to a known brand but with slight variations (for instance, @costco-special-offers.com rather than @costco.com). And always be wary of clicking on any links promising you cheap products or asking you to fill out a random survey to receive free services. Your friends can also be hacked — you should be very suspicious of any downloads or links that your friends send you. Always confirm with them directly through a trusted medium (e.g. telephone) that they sent you a file or link.
If you think the email is a scam, place the email in your spam folder (or report it as an unsafe email). If you’re given the option to block the sender, do that, too! Your email provider will remember this and prevent messages from that email showing up in your inbox.
Because your email account will have a lot of personal details, it’s important to keep the login details secure. The best way to do this is with a password manager, which will generate a complex password for your email account, securely store the password, and automatically fill it in when you log in.
I also recommend users enable two-factor authentication (2FA) with their email login, which requires users to enter a second form of authentication in addition to their password when they log in. Gmail offers 2FA compatibility — so when I log into my Gmail account, I have to enter my password and also a one-time code that is generated by my password manager. This means that even if my email password is stolen, my account can’t be broken into (except in the unlikely event that a hacker gains access to my password manager).
How to Protect Your Privacy and Stay Safe on Facebook
While Facebook is a great tool to stay in touch with family and friends, it’s also a tool for market research to track you all over the web. All of your activity on Facebook is being tracked, analyzed, and sold to advertisers and businesses, but all of your browsing outside of Facebook is also being logged.
Making Facebook as Private as Possible
Here are some quick tips to make sure that Facebook is monitoring as little of your information as possible, and to prevent random strangers online from looking at the pictures and content you post on your Facebook profile:
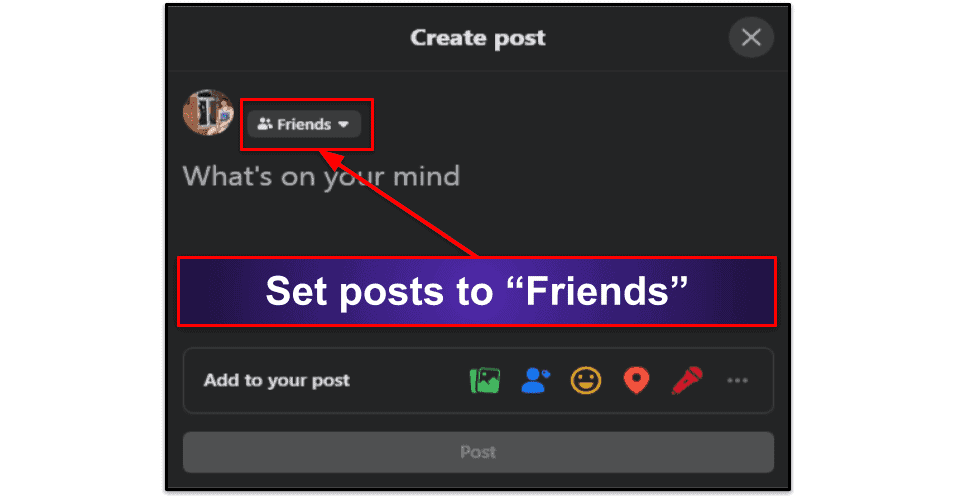
- Set your profile to “Friends”. If you want your personal Facebook profile (including all of the content you post on the platform) visible only to your friends list, simply select “Friends” from the drop-down list under your name in the “Write Post” box.
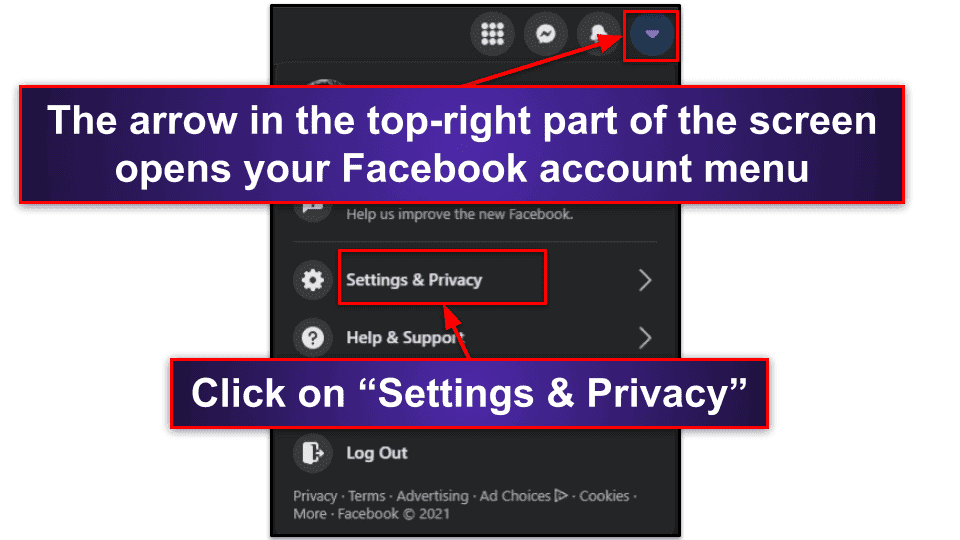
- Block off-Facebook activity tracking. To block Facebook from following you around the internet like a creepy stalker, you’ll need to deactivate “future off-Facebook activity”, which just takes a few steps.
- Select “Settings & Privacy” in your Facebook account menu.
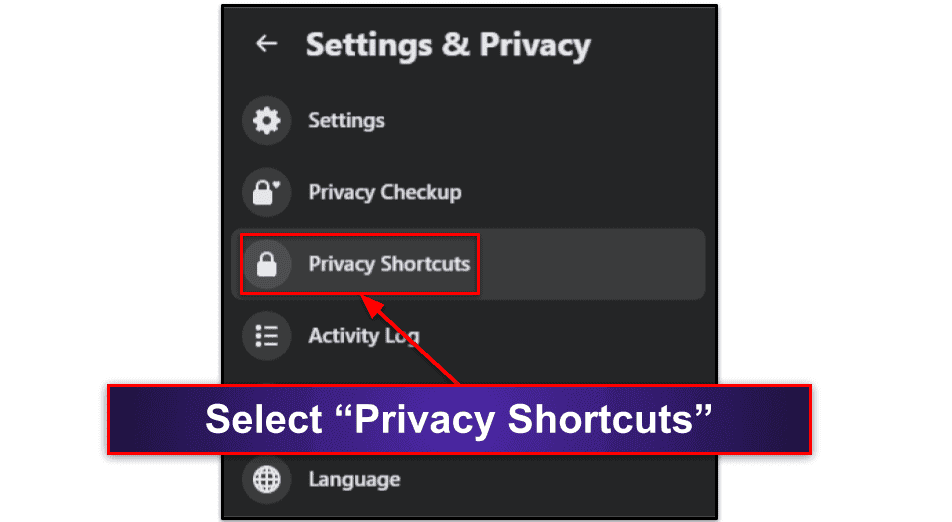
- Select “Privacy Shortcuts”.
- Under “Your Facebook Information”, select “View or clear your off-Facebook activity”.
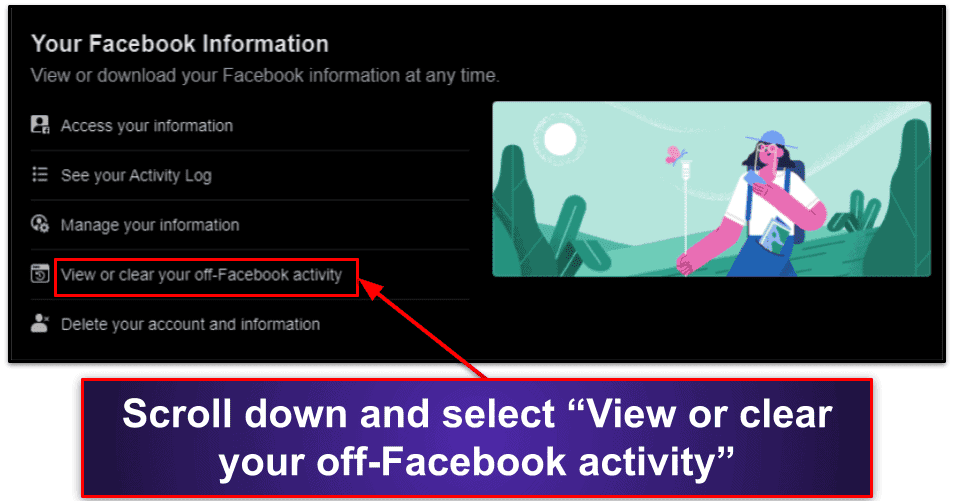
- First, select “Manage your off-Facebook activity”.
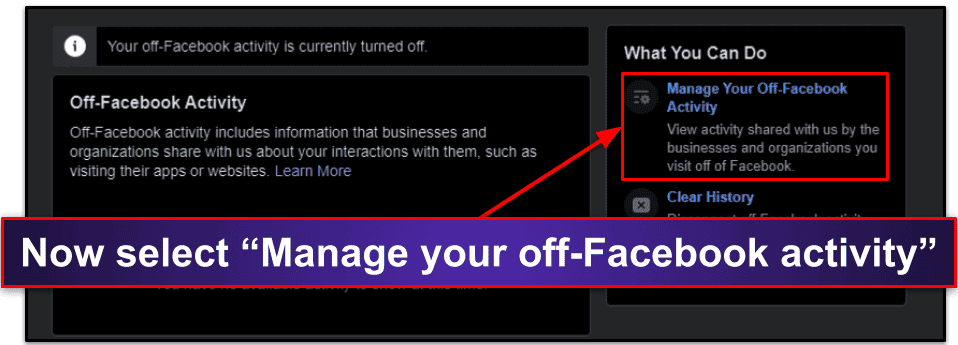
- Select “Clear History”, and then go to “Manage Future Activity”.
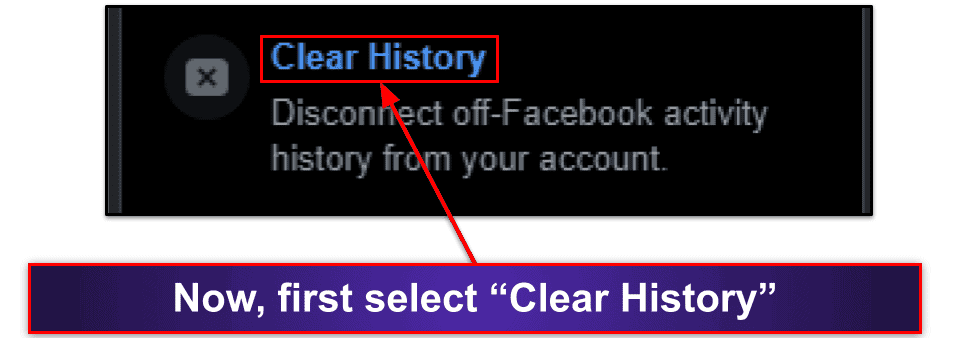
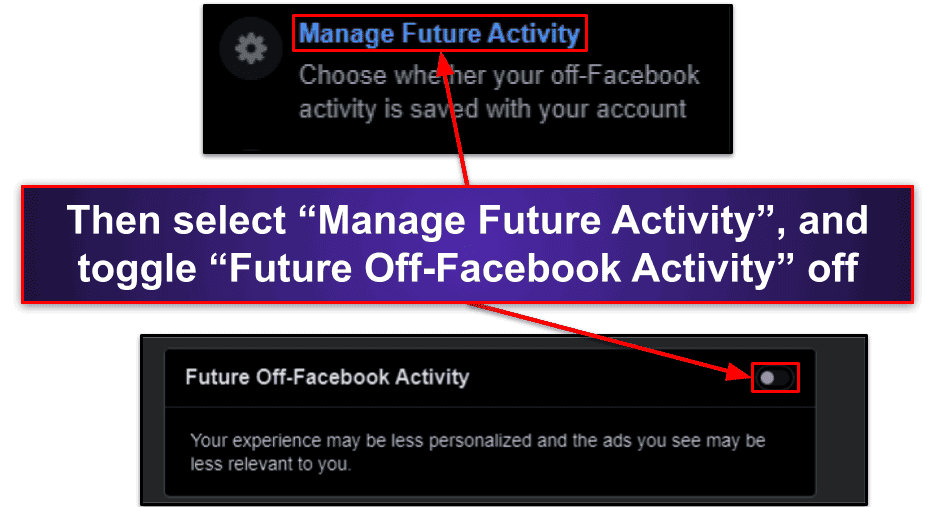
- And, finally, toggle off “Manage Future Activity” to prevent Facebook from tracking you around the web in the future.
Now that you’ve minimized the amount of data Facebook is gathering about you around the web, you can move on to preventing any cyberattacks while you’re actually using Facebook.
Staying Safe on Facebook
Cyber criminals are also able to take advantage of Facebook users by creating fake Facebook accounts and exploiting unaware individuals. If you receive any unsolicited communication or interaction from someone you don’t know on Facebook, whether it’s a message or a friend request, consider the following:
- The profile picture. Is there a picture that looks unique and confirms their identity, or are they using what looks like a random stock photo?
- Personal details. Check out how much information they’ve provided about themselves on their profile. Typically real profiles will have some personal details, while a cyber criminal won’t have any work history, family members, or life events listed.
- Followers/Friends. Look at how many friends/followers they have and if they’re interacting with them. A real person on social media will usually have a few friends or family interacting with them. A criminal will have very few or zero comments or posts from friends on their Timeline.
- Mutual friends. If you don’t have any mutual friends with someone, and you don’t recognize them, it’s probably a spam account.
In general, it’s not a good idea to respond to or engage with messages from people you don’t know. Criminals send out messages in the hopes of luring seniors to give up financial or personal information.
One of the easiest things to steal is a Facebook user’s account information. Once a user has been tricked into giving up their Facebook information, hackers will use the victim’s profile to spam friends with more junk links and surveys designed to steal more user data.
You’ve probably already seen what it looks like when Facebook accounts get hacked — users start posting and sending messages about sales, surveys, or job opportunities that are clearly generic or copy-pasted. If you try to message them back for more details, you don’t get any response! That’s because your friend’s account is now being run by a spam bot, which sends out automated messages in the hopes of hacking more users.
If you receive a strange message from a friend requesting that you send money, to click on an untrustworthy link, or other suspicious requests, delete the message. Then contact your friend immediately via a different communication method (phone call, email, text, or by informing a loved one with access to your friend) and confirm that they sent you the message. If they didn’t send you the message, they will know their account has been hacked.
Alos, if your friends inform you that they’ve received a suspicious looking message from you and you didn’t send it to them, you’ve probably been hacked. If this happens, immediately change your password. Then go to www.facebook.com/hacked and follow the steps there to secure your account ASAP.
How to Use Online Banking & Online Shopping Safely
Banking and shopping online through legitimate channels is very secure, but there are a few common mistakes that can cost you a lot of money. In 2020, IC3 reported that over $20 million was stolen from US seniors solely from credit card fraud.
Here are some tips to stay safe when you’re banking or shopping online.
How to Stay Safe When Banking Online
First, make sure you’re using your bank’s official website or mobile app. You can locate your bank’s website on the back of your debit or credit card, or on a piece of official correspondence sent from them (e.g. your monthly statement). Most larger banks have official mobile apps that you can download from the Apple App Store on your iOS device or Google Play Store on your Android device.
Once you’ve found your bank’s official website/app, setting up your online bank account will require you to have access to your routing number and account number. You will also need to use a strong password that is unique to that account. Don’t include any personal information in the password itself (for example, your birth date or name) and never share your full password with anyone. As I’ve mentioned above, a password manager is the best way to keep you protected — check out our favorite password managers.
If possible, don’t log into your online banking on a public network (like a coffee shop or a library) — only use a secure Wi-Fi network (like your home network) to access the account. By using an unsecure network, you may be vulnerable to hackers accessing your personal information. If you’re using a public computer, always make sure to log out of your online banking session when you’re done! The best way to keep your public internet use secure is to install a VPN on your device, which will encrypt all of your data with unbreakable 256-bit AES encryption (I think ExpressVPN is the best VPN on the market in 2023).
Another major threat for users that are accessing banking information online is keylogging. Keylogging is a dangerous type of malware that allows cyber criminals the ability to record everything that you type into your keyboard (even on mobile touch keyboards). Keyloggers can be particularly alarming when you’re typing in your bank account or credit card number into your bank’s website. Some hackers will even use the screen capture tools on your devices to record your on-screen activity and steal data that way (this is a process known as screenlogging).
The best way to combat keylogging and screenlogging is to use a good antivirus that can detect this type of malware. Bitdefender has excellent real-time malware scanning, and its Safe Pay tool includes a secure browser that blocks access to screen capture tools, as well as an on-screen keyboard that you can use to enter sensitive information online without having to touch your physical keyboard.
How to Stay Safe When Shopping Online

When shopping online, take the following safety precautions to purchase items securely:
- Don’t click on ads. If you see a nice deal on a third-party website, don’t click on the deal. Instead, go directly to the company’s website to ensure that the offer is legitimate.
- Use an online payment company account. Where possible, instead of entering your credit card information into a shop’s website, use a digital payment company like PayPal or Venmo as a middle man. By using a third party payment service like PayPal, you avoid giving your credit card information directly to the merchant.
- Stick with trusted brands. Instead of shopping on an unknown website for a good deal, stick with brands and retailers you’ve used before or that have a good reputation.
- Read reviews. If you’re unsure whether an online retailer is legitimate, read the reviews of the retailer online and decide for yourself if the website can be trusted — be wary if there aren’t any bad reviews, as this usually means a vendor is scrubbing their reviews to hide misconduct. Also check the site URL in Google’s Transparency Report to confirm that the site is safe to access.
Tracking Monthly Payments
Hooking users into a monthly subscription plan is a ubiquitous (and perfectly legal) technique used by businesses to get money from forgetful users. I didn’t even know I was still paying for Hulu almost 2 years after I had last watched a program on it! It can be extremely difficult to figure out what monthly payments are coming out of your account, and why. Here are some tips:
- Set up transaction alerts with your bank. Everytime your credit card is used, you’ll receive an email or text message. I like being able to search my emails for a specific transaction, which is way easier than using my bank’s interface.
- Use Mint to track your payments. Mint is an app and website that can be used to track payments across all of your cards and accounts, devise a budget, and label expenses so that you’re never confused about what you’re paying for.
- Track your app subscriptions on your mobile device.
- iPhone and iPad.
- Tap “Settings”.
- Tap your Apple ID at the top of the screen.
- Select “Subscriptions”.
- You can view and edit your subscribed apps here.
- Android devices.
- Select “Settings” > “Manage your Google Account”.
- Select “Payments & Subscriptions”.
- Tap “Manage Purchases” or “Manage Subscriptions”.
- You can suspend or cancel your subscriptions here and even try to get refunded for your purchases if you feel there has been an error.
How to Protect Your Privacy Online
Most websites use trackers on their webpages to gather data about what users are clicking on, how long they spend on certain pages, and much more. This data helps companies make their websites better for users and more profitable for businesses. The big problem is that many of these trackers continue monitoring you after you leave a website — many Facebook users are shocked to find out that Facebook is actually recording every website they click on.
This web tracking has become a pretty annoying part of the internet, and for many users it raises the important issue of online privacy and the consequences of what happens when it’s invaded. Even if you don’t mind that Facebook’s advertisers may be able to find out that you have a medical condition before you do (by tracking your searches and browsing history), there can also be security consequences if a substantial amount of your tracked data is released in a data breach.
An effective and easy way to protect yourself from these trackers is to download an ad-blocker and cookie/tracker blocker. Avira’s Browser Safety extension is my personal favorite — it’s free and available for Opera, Chrome, and Firefox.
Another effective option is to install a virtual private network (VPN) on your device. VPNs mask your internet protocol (IP) address and can hide your online activity from hackers and trackers. Many VPNs come with ad-blockers and cookie/tracker blockers as well. Proton VPN and Private Internet Access both have really good ad/tracker blockers.
If you’re a Google Chrome user, you’re vulnerable to a new advanced method of tracking called FLoC — short for “federated learning of cohorts”. FLoC was designed to be less invasive, but unfortunately, it’s still a disaster for online privacy. There’s currently no way to opt out of FLoC on Chrome. The best way to avoid FLoC is to use a more secure browser, like Firefox, and start using a privacy-oriented search engine like DuckDuckGo instead of Google.
To see if FLoC is being used on your browser, you can use our FLoC Checker Tool.
How to Prevent Malware & Viruses from Infecting Your Device

Malware is an umbrella term to encompass any program or code that is harmful to a computer system. Malware is unfortunately very common, with 2.5 billion malware attacks being recorded in the first half of 2021. Malware attacks can range from devastating attacks to minor nuisances, and many types of malware can infect your device without you ever noticing that you’ve been compromised.
Here are some of the most common types of malware:
- Virus. A malicious program that repeatedly copies itself, taking up space on your hard drive and causing your computer to crash.
- Trojan. Pretends to be a legitimate file to gain unauthorized access to your device in order to steal data, install other malware, or even give hackers remote access to your computer. Trojans are very common, accounting for 58% of all computer malware attacks in 2020.
- Spyware. Allows hackers to quite literally spy on your computer and track your browsing history online.
- Adware. Clutters your desktop with pop-up ads, inserts unwanted results in your search bar, and even redirects your browser while you’re online.
- Ransomware. Encrypts and locks your device unless you pay a ransom to recover your account. In 2020, ransomware attacks cost Americans over $29 million!
- Rootkit. Gains extremely deep access to your system, allowing it to hide from antivirus scanners and make changes to the operating system and other essential components.
- Cryptojacker. Uses your computer as part of a larger network to mine cryptocurrency. This can put a ton of strain on your computer, causing slowdown, crashing, and even permanent damage to your hard drive. Over 50 million cryptojacking attacks have been reported in the first half of 2021 alone!
To protect yourself against these types of malware and others, it’s important to use safe practices when browsing online. For instance, don’t download email attachments from people you don’t know, don’t download files from untrustworthy websites, and of course, download a good antivirus program.
Diagnosing and removing malware manually from a computer is an extremely complicated and time-consuming task — and you can actually do significant harm to your device while trying to remove malware. If your computer is running slowly, you’re seeing strange pop-ups, or you’ve been navigating to unsafe websites, you need to run an antivirus scan.
Antiviruses offer on-demand malware scanning to remove existing malware on your computer, and they also provide real-time threat detection to block malware files before your system is compromised. Norton is my favorite overall antivirus, but TotalAV is also a great option, especially for beginners looking for an exceptionally easy-to-use program with a decent free version.
Check out our list of the 10 best antivirus software in 2023 to decide which antivirus program is best for you.
How to Stay Safe on Your Smartphone & Tablet

Smartphones are basically pocket computers, so all of the threats we’ve discussed above also apply to Android devices, iPhones, iPads, and even smart watches. I’ll quickly cover a few mobile-specific threats in this section, though.
Mobile Malware
Although not as common as computer threats, malware on mobile devices occurs often — on average, 480,000 new Android malware files were recorded every month in 2020. Apple’s iOS products can’t get most traditional malware files — it’s part of the super-strict design and protocols involved with developing apps for Apple’s App Store. The best way to stay safe on iOS is to make sure you keep your device updated.
However, Android devices can get infected with ransomware, spyware, trojans, and a variety of dangerous malware files. In fact, the supposedly secure Google Play Store is one of the most common sources of Android-based malware.
There are some great Android security apps that can analyze all of the apps and files on your device to determine if you have malware running — McAfee is my favorite, but Norton’s mobile security app is also really good.
Privacy-Invading Apps & Fleeceware
A lot of apps may not qualify as malware, but they are designed to steal your information and trick you into overpaying for them. The practice of using apps to gain access to a user device and steal data is known as permission abuse.
There are a lot of apps on both the Google Play Store and the Apple App Store that ask for a lot of user permissions to run on your phone. You should always be skeptical of these kinds of requests, because permission abuse is a huge problem with mobile apps — they steal browsing data, track your location, monitor your app usage, and more, all in an effort to harvest data and sell it online. You should only download apps that you feel 100% comfortable with.
Security apps like Avira Mobile Securitycan analyze and flag apps that are suspected of permission abuse, making it easy to see what information your apps have access to.
You should also be on the lookout for fleeceware applications. These apps advertise amazing results and free trial periods, but they’re actually extremely basic, and they include ridiculously overpriced subscription plans. For example, one fleeceware app claims to do accurate palm readings — it comes with a 3-day trial, and then charges users $50 a week after that! There are fleeceware astrology apps, photo editors, calculator apps, and so many more. Recent studies have shown thousands of fleeceware apps in both Apple’s App Store and the Google Play Store. Read our complete guide on fleeceware scams to ensure you don’t get stuck with a big bill.
Public Wi-Fi Networks
Public Wi-Fi networks can be a great resource for free internet access, but hackers can use public Wi-Fi to invade your devices. If you connect to public Wi-Fi, you should always make sure that you’re connecting to the correct network (ask an employee at the library, coffee shop, etc. what the network is called), and don’t navigate to banking sites or enter any financial information online.
Many mobile security apps include Wi-Fi scanners, and many of the top VPNs on the market are a great tool to protect your data on public networks — they can flag unsafe Wi-Fi networks and also encrypt your traffic and protect your privacy while you’re browsing on a public Wi-Fi network.
Smishing
Smishing is a type of phishing attack that targets SMS users (SMS is better known as text messaging). These seemingly urgent messages will try and induce users to click a link by threatening victims with legal action or promising them rewards. The last few years have seen an incredible rise in the number of smishing attacks. You should never follow a link in a text message from an unknown phone number. And always follow up through legitimate channels if you think you’re being contacted by an untrusted source.
Most smishing messages will be pretty easy to figure out. They often say things like, “Your Amazon delivery is here, click this link to verify Vn78jy.azn”. Be wary of text messages — follow my steps above for phishing messages and get a mobile security app like Bitdefender with real-time web protections that can block phishing links before you open them.
Staying Safe
To reduce the security risks associated with mobile devices, ensure you only download apps from authorized app stores — for Apple it’s the Apple App Store, and for Android it’s Google Play. Most importantly though, install an antivirus security app onto your device.
Some good features to look out for in mobile antivirus programs are:
- Real-time malware protection.
- App privacy detection.
- Wi-Fi monitoring.
- Parental controls.
- Anti-phishing protection.
- VPN.
- Anti-theft protection.
Norton is my favorite internet security app for iOS and Android, but you can check out our top mobile antivirus guides for iOS and Android and decide for yourself.
Bottom Line

While you can’t stop cybercrime, you can take many precautions to avoid becoming a target and greatly reduce your chances of becoming a victim.
Keep in mind some of the key ways to stay safe online:
- Download an antivirus program. Install a good antivirus on your computer and mobile device to protect yourself from malicious threats online. Norton and McAfee are great options.
- Don’t click on pop-ups or suspicious looking links. Whether it’s an ad or a link from an unknown sender, it’s not worth the risk of infecting your device or compromising your personal information. Delete the message and close the pop-up.
- Use a password manager. One of the most effective things you can do to be safe online is to secure your accounts with a strong, unique, and complex password. You can create good passwords with a password generator and also keep track of your passwords with a password manager. 1Password is my personal favorite.
- Keep your system updated. Make sure to stay on top of update notifications from your computer or mobile device. They are critical in patching up new security vulnerabilities and for keeping you safe from exploit attacks.
- Have a tech support friend. Whether it’s a family member, caregiver, or neighbor, don’t be afraid to reach out and ask for help if you think you may be the subject of an online attack.
- Use common sense and be critical. If it’s too good to be true, it probably is. Before you download a file or click on a link, consider if the website or source is trustworthy.
- Download a VPN. A good VPN can greatly enhance your privacy online, especially while you’re using public Wi-Fi. ExpressVPN is my favorite all-around VPN, and you can learn more about VPNs here.
FAQs — Internet Safety for Seniors
- How can I keep myself safe from online threats?
- What are the best ways to keep my financial information safe when online shopping?
- How do I protect my privacy online?
- What can caretakers do to help seniors stay safe online?
How can I keep myself safe from online threats?
The best way is to use common sense when browsing online, install an antivirus program, and use a password manager and a VPN.
Common sense means: Don’t follow links from suspicious sources, be mistrustful of messages or websites that ask for personal information, and reach out to a more knowledgeable person if you’re feeling unsafe online.
An antivirus suite like Norton is easy to use and will offer you advanced protection against malware, phishing threats, and so many other forms of cyberattacks.
A good password manager is a great tool — it creates virtually unbreakable passwords for each of your accounts online and stores all of your passwords in an encrypted vault so you will never forget your passwords (1Password is my favorite password manager).
A VPN hides your actual IP address from hackers, masks all of your online activity, including the websites you visit and the files you download, and protects all of your data with military-grade encryption. ExpressVPN is the best VPN on the market in 2023.
What are the best ways to keep my financial information safe when online shopping?
You should never click on ads, use a third-payment service like PayPal, routinely monitor your bank accounts, and only visit trusted websites to keep your financial information safe.
Ads on social media, pop-up ads, and even sponsored posts on the top of Google searches can frequently take you to unsafe or sketchy websites. It’s best to simply go to the website of the vendor you’re searching for than to try and navigate there using ads. Many antivirus suites like Bitdefender and Norton also include web shields that can block unsafe websites.
Online payment services like PayPal and Venmo add an extra layer of protection — you won’t give your credit card number directly to a merchant. Further, only shop on trustworthy websites — ones you’ve purchased from before or are highly rated. You can look for user reviews on Google or even Reddit to get a better idea about an online vendor’s quality.
And make sure to keep on top of the transactions in your bank accounts (you could even consider contacting your bank and activating transaction notifications for your accounts). Report any unauthorized activity to your bank as soon as you can, and follow my tips above to stay safe if you think your identity has been stolen.
It’s advisable to use a password manager to secure accounts you make on retailer websites. Create strong, unique passwords and store them safely. There are many great password managers to choose from — my top pick is 1Password.
How do I protect my privacy online?
The best way to protect your privacy is to prevent trackers from monitoring your online activity with an ad-blocker and cookie/tracker blocker. By installing a blocker to your browser, you will prevent websites from recording your activity and selling it to third-parties. Avira’s Browser Safety extension is my personal favorite — it’s free and available for Opera, Chrome, and Firefox.
Many VPNs also come with built-in tracker blocking tools, and they encrypt your internet connection to make it harder for hackers and big businesses to track you online. Private Internet Access and Proton VPN are excellent VPNs with tracker-blocking capabilities.
For Chrome users, FLoC (federated learning of cohorts) is a new method of tracking online activity. We have prepared a guide about FLoC to inform users and provide protection advice.
What can caretakers do to help seniors stay safe online?
You can assist a senior to stay safe online by helping them install easy-to-use programs and online tools to protect their internet activity.
In addition to referring to this article to get a better idea of the risks facing seniors online today, it’s also a good idea to purchase a top antivirus (Norton), password manager (1Password), and VPN (ExpressVPN).
Moreover, answer any questions or concerns they may have and keep a close eye on their social media accounts and banking activity to help keep your loved ones safe online.
Source: www.safetydetectives.com, Ben Martens